How Vendor Data Breaches Are Putting Law Firms at Risk
Records show that law firms' relationships with third-party vendors are a frequent point of exposure to cyber breaches and accidental leaks.
October 17, 2019 at 05:45 PM
11 minute read
 (Image: Shutterstock)
(Image: Shutterstock)
In the early morning hours of Oct. 10, 2012, a laptop belonging to accounting firm WeiserMazars, a vendor to Blank Rome, was stolen from an employee's car in Philadelphia.
That triggered a series of letters from Blank Rome notifying state officials and others that the incident may have exposed the personal information of the law firm's personnel, affecting nearly 60 people.
"A file on the laptop may have included your name and social security number," according to a template letter signed by a Blank Rome attorney and sent to affected individuals. "Because the incident may have compromised this personally identifiable information, we are bringing this situation to your attention."
Also in This Series:
More Than 100 Law Firms Have Reported Data Breaches. And the Problem Is Getting Worse
While law firms are often considered a weak point in the security of corporations' sensitive information, firms or their employees have frequently suffered potential leaks through their own third-party vendors, according to Law.com's investigation of law firm data breaches across the country. The breaches that law firms reported to state authorities varied in severity, and some incidents were unrelated to the strength of the law firm's cyber defenses and didn't risk or relate to client data.
External breaches, including phishing and hacking as well as vendor incidents, were the most commonly identified source of data exposure events reported by law firms, according to Law.com's investigation, which examined data breach notifications from more than a dozen states. Stolen or lost devices were the second most common type of security incidents reported by law firms.
In the case affecting Blank Rome, the firm told New York state officials that WeiserMazars, now called Mazars, was investigating the incident and had notified law enforcement authorities.
A Blank Rome representative declined to comment to Law.com, citing client confidentiality. A spokeswoman for Mazars said it abides by ethical and professional rules and "is diligent with adhering to our duties and obligations to clients, which include comprehensive internal controls." The company, now in the headlines for its accounting work for President Donald Trump, declined to comment further.
Less than two years after that incident, in early 2014, Jeff Haidet, then chairman of McKenna Long & Aldridge, told New York state officials that the personal information of about 1,300 people could have been affected in a security breach.
The firm learned of "suspicious computer activity on servers" belonging to a vendor and that "some information related to current and former employees was accessed" around Thanksgiving Day through the unauthorized use of an administrator's login credentials, according to the letter from Haidet, now U.S. chairman of successor firm Dentons.
In a statement to Law.com, a Dentons spokeswoman confirmed that, about six years ago, the systems of a former vendor of McKenna Long were breached. However, she said, a thorough investigation "confirmed that no McKenna Long systems were improperly accessed."
More recently, Philadelphia litigation boutique Goldberg, Miller & Rubin reported that it learned in October 2016 that a security researcher was able to access electronic files relating to some of its cases. It appeared that a "service provider made an error in configuring the backup device," the firm reported to state authorities.
"We have the data because we represented you or another party in a claim or lawsuit," the firm said in a template letter to those affected.
A partner at Goldberg Miller declined to comment.
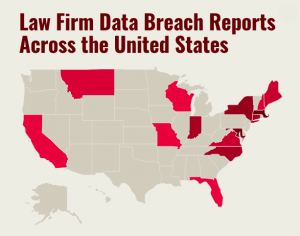 Click the image to see which law firms reported breaches.
Click the image to see which law firms reported breaches.According to Law.com's analysis, several large firms reported that their employees were potentially affected through corporate breaches that made national news. For instance, Jones Day reported that an unauthorized individual gained access to the reservation system of Sabre Hospitality Solutions, a third-party vendor for the firm's travel services provider, between August 2016 and March 2017.
"This was not an incident that was suffered by the firm or by our travel agency, it was by a vendor of the travel agency," said Jones Day partner Mauricio Paez in an interview, adding his firm submitted the security report because the state statute requires that the entity that actually has the relationship with the employees and who engaged the third parties is responsible for notifying employees. "We just forwarded the notice that we received from Sabre Hospitality Solutions."
The firm continues to "vet any third-party provider for their own security controls and information security program," Paez said.
Both McDermott Will & Emery and Akerman reported in 2015 that their firm's participants in group health plans could have been affected by a widely reported Anthem cyber hacking that year. A McDermott representative declined to comment. Akerman representatives did not respond to requests for comment.
Jon Washburn, the chief information security officer at Stoel Rives, said the legal community has become more attuned to the risk of vendor threats, with many firms ramping up their efforts to address third-party risk.
Some law firms now require that vendors that access, store, process or transmit confidential information be able to demonstrate through certifications or reports that the vendor has strong controls in place to reduce the risk of a data breach, Washburn said.
In addition, some law firm clients are now including third and even fourth party risk management requirements in their outside counsel guidelines and representation agreements, Washburn said.
From the Complex to the Routine
Besides external breaches, law firm data security incidents ran the gamut from ransomware attacks to stolen hard drives to mixed up letters in the mail, according to the data breach reports obtained by Law.com.
Some data breaches were surprisingly sophisticated in capturing client data.
Texas boutique Schachter Harris reported in 2017 that it was subject to an attack by "unknown criminals" that could have affected people who filed or were involved in lawsuits alleging asbestos-related injuries.
"The attackers used encryption ransomware to make some information on our computers inaccessible to us," the firm told authorities. "When we did not pay the ransom, the criminals claimed to possess the data from our computers. Based on our investigation, we believe that the attackers were able to acquire some files stored by our firm, relating to at least one of our clients."
In an email responding to Law.com's inquiry on the matter, partner Ray Harris said "this was a serious crime" and "the criminals to our knowledge, have not been caught." The firm declined to comment further.
Some law firm theft incidents were also reported to have exposed client data. One of the largest law firm breaches Law.com found, as measured by the number of people reportedly affected, was at a Los Angeles criminal defense firm, Imhoff & Associates, which notified authorities in at least six states that a hard drive containing backup files for one of the firm's servers was stolen from the locked trunk of an employee's vehicle.
In its notification letter, Imhoff, which worked with the Santa Monica Police Department and forensic experts, said "the hard drive may have contained files with differing amounts of employee and client information," such as Social Security numbers, driver's license numbers and contact information. The firm reported to New York officials that personal information from 13,026 people could have been exposed.
In an interview, the firm's managing director, Vincent Imhoff, said he doesn't "think any information was actually breached," but confirmed that "they took an external hard drive from the trunk of my car."
Imhoff said his firm has changed the way it stores information, declining to discuss details. He said his firm has been working with a third party to ensure cybersecurity since 2016.
As the Imhoff event demonstrated, some of the most troubling security incidents occurred when law firms never learned what happened to missing devices.
Ice Miller, in letters in 2016 sent to affected individuals, said a firm employee took a hard drive with files on it home to continue working on it, but that "the hard drive was stolen from her residence along with other personal belongings by her estranged husband."
The law firm concluded that her estranged husband had no interest in the Ice Miller files, but the hard drive contained certain IRS forms, "which, in turn, may have contained your social security number," the firm said in its notification letter.
In a statement to Law.com, Ice Miller said that although the hard drive was not recovered, the firm "determined the hard drive was likely destroyed and no confidential nor personal information was accessed. Only a very small number of people were affected, and the firm reached out to each of them individually." (The firm reported to state authorities that 52 people were affected.)
Other large firms also reported theft. In 2012, Wilson Sonsini Goodrich & Rosati told Massachusetts officials that it became "the victim of a computer equipment theft" and that the stolen equipment "contained unencrypted personal information," including a person's Social Security number.
In a separate incident, Wilson Sonsini reported in 2011 that a "small number of our computers used to process customer orders were infected by a previously unknown virus."
A Wilson Sonsini spokeswoman confirmed to Law.com that the "data breach incidents happened at the firm." In a statement, Jeff Lolley, Wilson Sonsini's chief information security officer, said the firm took appropriate steps "to inform the proper authorities regarding these minor incidents." He added, "We also take very seriously our obligation to protect our client and employee data, as we did then, and continue to focus on implementing technology and process solutions that not only meet, but exceed regulatory and client requirements for data protection and privacy."
Still, not all data breaches were malicious or deliberate widespread attacks. Several law firms reported paperwork errors on the part of firm employees and attorneys, such as sending the wrong document to a client or inadvertently including personal information in a court document.
Fragomen reported to New York state authorities in 2014 that a law clerk at the firm shared certain information with another law firm "without the firm's authorization," affecting one person. Meanwhile, Squire Patton Boggs informed state authorities last year that, when mailing out tax forms, it "mistakenly" mixed up documents in an envelope, possibly affecting 256 people. Mintz, Levin, Cohn, Ferris, Glovsky and Popeo reported last year than a human resource employee, responding to an employee's request for a W-2, "inadvertently sent an email and attachment to someone with a similar name outside the company."
In a statement, Fragomen said the incident was an "extraordinary event, which occurred a half-decade ago as the result of a single employee's willful and confined malfeasance." The firm said it is "in no way indicative of the robust cybersecurity guidelines and practices Fragomen has long had in place" and that it was fully committed to safeguarding clients' personal information. Squire Patton Boggs and Mintz Levin did not return messages seeking comment.
Ultimately, whether it was a cunning hack or a missing laptop leading to a breach, law firms often responded the same way: hiring forensic experts to track and assess the exposure, training staff on prevention and implementing new cybersecurity guidelines.
Large firms often dedicate vast resources and time to maintaining high cybersecurity standards, said some cybersecurity experts, but they note criminals and hackers are also becoming more sophisticated.
"They're moving at an equal pace," said Claudia Rast, Butzel Long's cybersecurity group leader and a member of the American Bar Association's cybersecurity legal task force. "The bad guys are moving as quickly as we are."
This article is the second in a Law.com series focused on law firm data breaches. Next up: How law firms have ramped up cybersecurity efforts, and what weaknesses remain.
Samantha Stokes contributed to this report.
Read More:
More Than 100 Law Firms Have Reported Data Breaches. And the Problem Is Getting Worse
Law Firm Cybersecurity: See Which Firms Reported a Data Breach
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All
12-Partner Team 'Surprises' Atlanta Firm’s Leaders With Exit to Launch New Reed Smith Office
4 minute read
After Breakaway From FisherBroyles, Pierson Ferdinand Bills $75M in First Year
5 minute read
Wells Fargo and Bank of America Agree to Pay Combined $60 Million to Settle SEC Probe
Trending Stories
- 1How ‘Bilateral Tapping’ Can Help with Stress and Anxiety
- 2How Law Firms Can Make Business Services a Performance Champion
- 3'Digital Mindset': Hogan Lovells' New Global Managing Partner for Digitalization
- 4Silk Road Founder Ross Ulbricht Has New York Sentence Pardoned by Trump
- 5Settlement Allows Spouses of U.S. Citizens to Reopen Removal Proceedings
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250









