Will Data Security See a '90s Throwback + YouTube Dodges Public Forum Fight + People Are Mad at Mark Zuckerberg, Again Will Data Security See a '90s Throwback + YouTube Dodges Public Forum Fight + People Are Mad at Mark Zuckerberg, Again
Here's a sneak peak of what the world might look like if the biggest tech platforms were forced to grant access to law enforcement.
October 30, 2019 at 09:00 PM
13 minute read
Welcome back for another week of What's Next, where we report on the intersection of law and technology. This week, we continue our conversation about encryption backdoors by envisioning what the world would look like if the biggest tech platforms were forced to grant access to law enforcement. Plus, a judge shuts down Prager University's "excellent arguments" over YouTube censorship. And Mark Zuckerberg gets a warning from Congress. Let's chat: Email me at [email protected] and follow me on Twitter at @a_lancaster.
SPONSORED BY ALM
Rod Rosenstein Keynotes Legalweek New York 2020
From Rod Rosenstein to a Live Newsroom, here's a taste of the big and small in what's new at Legaltech and Legalweek New York in February. READ MORE

Backdoors Wide Shut
Last week, we discussed just how backdoors to encryption might come about. Now, we're taking a look at the potential consequences that could follow as a result.
Stewart Baker, a partner at Steptoe & Johnson's office in Washington, D.C., said a world with backdoors wouldn't be quite as dreary as the one the tech community has painted over the years. In fact, it would look a lot like the pre-encryption era of the 1990s.
"I think Silicon Valley and their advocates have prepared us for the belief that it's some dark dystopian nightmare," the former general counsel of the National Security Agency said. "It actually looks a lot like the '90s, and so if the '90s were a dark, dystopian nightmare for you, maybe that's not comforting, but most of us lived through it pretty well."
However, Riana Pfefferkorn, associate director of Stanford Law's surveillance and cybersecurity program, said she doesn't think it would be as simple as rolling back encryption.
"I don't think it's going to be the same as waving a magic wand and having everything go back to the way it was five years ago," she said.
In addition to extensive reengineering, the costs and logistics of fielding a flood of law enforcement requests could have economic effects, she said.
"The fact that there are tens of thousands of law enforcement agencies around the world—there are 18,000 in the United States alone—trying to scale that up means that only existing, entrenched incumbents will be able to comply with the compliance structure," she said. "Some handset manufacturer in Taiwan is not necessarily going to be able to scale up to that."
Amie Stepanovich, executive director of the Silicon Flatirons Center for Law, Technology, and Entrepreneurship at the University of Colorado Law School, said that tech companies would be forced to decide who could use these features and under what circumstances. In Apple v. FBI, where the government asked the company to create a backdoor for the iPhone after the San Bernardino shooting, other groups tried to make their case for why they should have a key. "Cy Vance, the New York DA, said we have 400 iPhones in New York that we would also like to get into," Stepanovich said. If backdoors to encrypted products became universal, the cryptography expert expects to see similar scenarios, where officials from the FBI all the way down to local law enforcement try to get in, requiring the tech community or regulators to set usage limits.
After the U.S. adopts widespread backdoor encryption, the tool would likely spread throughout the world, Stepanovich said. "I think we would see a lot more countries emulating what we had done, and not countries we would necessarily want pushing companies to change their products and services," she said.
The professor pointed to China's 2016 cybersecurity law, which has potential ramifications for encryption, as an example. When it was passed, Chinese officials told media the U.S. already had this authority, and they just wanted it for China as well, she said. "People copy what we do, and it can have huge impacts on the protection of human rights and digital security," she said.
Besides, the well-known security risks of handing out access to encrypted products, Stepanovich also pointed to compounded vulnerabilities in the future from backdoor access that's introduce today. For instance, the FREAK bug, a security exploitation discovered in 2015 that exposed Apple's Safari web browser, Microsoft's Internet Explorer and Google's browser in its operating system, was a direct result of the export controls on encryption that were in place as early as the 1970s, she said. "We could create huge issues down the road that we couldn't even fathom right now," she said. "So I think we'll see pretty immediate beginning of the increase in vulnerabilities and incidents, and I think down the road we would see those get bigger."

The End of the Road for Prager U.'s Free Speech Suit Against YouTube?
Prager University's lawsuit accusing YouTube of censoring its videos hit a dead end in a California state courtroom last week. However, the conservative organization's lead counsel from Browne George Ross said he has multiple backup plans to advance the case.
Judge Brian Walsh of Santa Clara Superior Court issued a tentative order denying the political content creator's motion for a preliminary injunction against YouTube.
Prager University, which conservative talk radio personality Dennis Prager founded a decade ago, claimed YouTube's restriction and demonetization of several dozen of its videos violated the nonprofit's rights under California's Unruh Act, the federal Lanham Act, and the state constitution's speech and association statutes, according to the first amended complaint filed in May.
Last Friday, Prager University's lawyers and YouTube's Wilson Sonsini Goodrich & Rosati legal team presented what Walsh called "excellent arguments" before an overflowing courtroom in San Jose.
In his tentative ruling, the judge wrote that Prager failed to state a claim under the California Constitution by arguing that the platform had the responsibility to protect users' speech, even in Restricted Mode, which hides some of PragerU's videos from institutions that opt in, such as schools and libraries.
"Prager contends that 'YouTube is the cyber equivalent of a town square where citizens exchange ideas on matters of public interest' and that defendants have opened their platform to the public by advertising its use for this purpose," he wrote. "However, Prager does not allege that it has been denied access to the core YouTube service."
YouTube also invoked Section 230 of the Communications Decency Act, as well as the company's First Amendment rights, in its notice of demurrer, writing that the laws safeguard YouTube's ability to make editorial decisions. Prager, on the other hand, had argued companies should not be able to hide behind the CDA when acting in "bad faith."
Walsh, again, agreed with the social media giant.
"While Prager contends that section 230(c)(1) immunity should not be applied where a plaintiff alleges a service provider acted in bad faith or to stifle competition, it cites no persuasive authority adopting this interpretation," the judge wrote.
The judge's ruling does not necessarily mark the last stop for this case.
If Walsh holds his tentative ruling, Peter Obstler, of Browne George Ross in San Francisco, said after the hearing that he'll appeal the case to the Sixth District Court of Appeal. Obstler said he's considering amending the complaint with antitrust claims, as well.
Obstler also warned Walsh during the hearing that he might end up right back in his courtroom.
While Obstler waits to appeal the case with the Sixth District, he said he's moving forward on another lawsuit that makes similar claims, but for LGBTQ plaintiffs. Obstler represents the hosts of LGBTQ news show "Glitter Bomb" in a suit against YouTube in the U.S. District Court for the Northern District of California. Its videos were restricted and demonetized for "shocking" content. When the channel's owners asked a Google representative why they were unable to buy ads for their Christmas special, the manager said "the major reason is because of the gay thing." Obstler said he has a recording of that conversation. The "Glitter Bomb" case is going to "push the limit on the CDA," Obstler said during Friday's hearing.
In the hallway outside the courtroom, Obstler said he's under no illusions about the road ahead.
"This is a very difficult case," he said. "We're going to settle a lot of law. If I can't win on this case—if I can't win on the LGBTQ case—then, basically, they can do what they want."

An Abbreviated List of Why People Are Yelling at Mark Zuckerberg, This Time
Mark Zuckerberg got an earful from lawmakers last week when he testified in front of the House Financial Services Committee, a piling on that followed him into this week with the announcement of a curated Facebook news tab that's set to go live Friday.
The committee questioned Zuckerberg on how cryptocurrency platform Libra might impact the finance and housing sectors. The Facebook CEO assured House representatives that he would not launch the payment services without the nod from regulators.
Yet, many people weren't quite convinced that the company, whose slogan was once "Move fast and break things," would wait on regulators to sign off. Zuckerberg said at least 10 times within the first two hours of the hearing that Facebook and Libra will not bring the product to market without approval from U.S. regulators.
Rep. Brad Sherman, D-California, questioned Zuckerberg's definition of "regulatory approval."
"Your lawyers are going to show that there's a loophole in a 1940s investment company act that gets you where you want to go, and the regulators can't stop you," Sherman said. "And you're going to call that regulatory approval as if the people of 1940 knew what you had in mind. What you've made clear is you will go forward unless Donald Trump-appointed regulators stop you, and you will go forward if you can find loopholes in statutes."
Sherman also warned Zuckerberg not to rely on lawyers urging him to move forward.
"I know you've got at least 100 lawyers that will tell you what you're doing is legal and that you will be safe," he said. "Given the harm that this can do, they can be really wrong. If this explodes the way it might, you won't be able to hide behind the idea that you didn't create the Libra organization."
But Zuckerberg was not just questioned about his plans for Libra.
Rep. Ann Wagner, R-Missouri, asked him what Facebook plans to do about child exploitation on its platform after the company rolls out end-to-end encryption, which could bar even Facebook from reading messaging between users on its platforms. "If you enact end-to-end encryption, what will become of the children who will be harmed" because of Facebook's inability to access and report predatory communications? she asked.
Zuckerberg said he, too, was worried "it will be harder to find this behavior" with end-to-end encryption in place.
Wagner also asked Zuckerberg to address reports that 16.8 million of the 18.4 million worldwide instances of illicit material involving children involved Facebook content.
"We built a sophisticated system to find this behavior," he said. "I don't think Facebook is the only place on the Internet this is happening. I think the reason the vast majority of those reports come from us is because we actually do a better job than anyone else in finding it and acting on it."
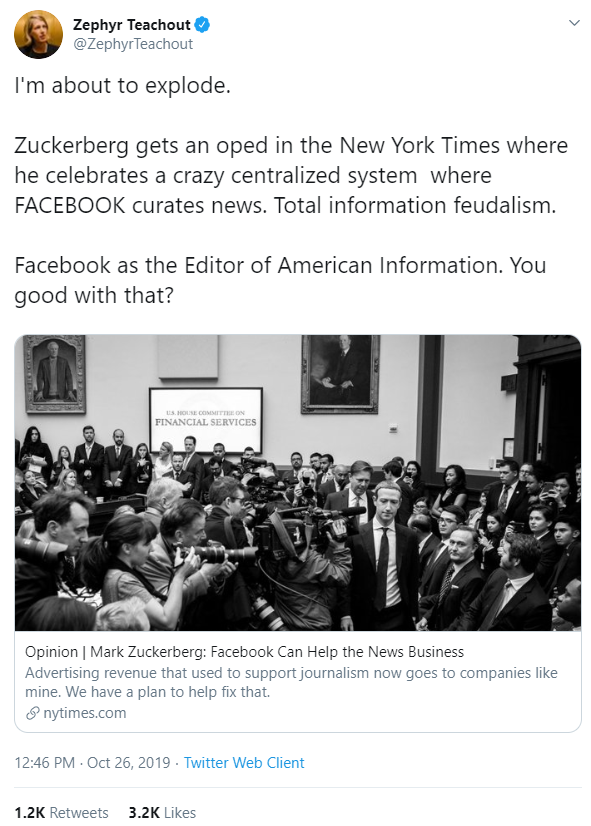
Facebook is also under fire for its news panel, which Zuckerberg announced during the hearing. Some critics took issue with which media would be included in the journalism tab, such as far-right news site Breitbart, while others questioned the idea of giving such editorial power to Facebook.
Zephyr Teachout, associate professor of Law at Fordham University in New York called the feature "total information feudalism" in a tweet. "Facebook as the Editor of American Information. You good with that?" she wrote.
Click to read the full thread:

On the Radar
A Deluge of Data Requests Ahead Recent agreements between the United States, the United Kingdom and Australia to expedite the sharing of digital data could increase the number of incoming requests from law enforcement overseas, according to Chris Ott of Davis Wright Tremaine. The partner predicts this is just the beginning of executive agreements that will spawn their own complex oversight and review frameworks. Read more from Chris Ott of Davis Wright Tremaine here. Privacy Protection Pioneers It's not exactly a shocker that California, whose comprehensive privacy protection law takes effect in January, was ranked No. 1 when it comes to shielding consumers from threats to their privacy, according to a study by technology research firm Comparitech. However, two of the states that landed in the top five—Utah and Arkansas—surprised some members of the law community. Although the states have passed enough privacy protection provisions to earn them a top spot, "just having a law on the books doesn't mean a whole lot by itself," said David Shonka, a partner in the Washington, D.C., office of Redgrave. Read more from Sue Reisinger here.
Can Law Firms Hack It? Some cybersecurity experts say it's not hardware or software that makes protecting law firms from threats more difficult, it's lawyers and other staff. Many law firms are working to train team members to keep up with more sophisticated hacking methods, such as phishing attempts that use email accounts of vendors, personal contacts or clients. Another vulnerability is that security procedures aren't always applied to senior management or rainmakers, said Frank Gillman, a former chief information security officer at Lewis Brisbois Bisgaard & Smith. "Those people oftentimes are the ones who are actually touching the most sensitive things," he said. "You've got a security framework, but the very top of that food chain isn't always part of that culture." Read more from Christine Simmons and Xiumei Dong here.
Thanks for reading. We will be back next week with more What's Next.
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All

What's Next: Judge to Quash Twitter Subpoena | SCOTUS Won't Review Trial Ban
4 minute read

Trending Stories
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250








