More Than 100 Law Firms Have Reported Data Breaches. And the Problem Is Getting Worse
A Law.com investigation finds that law firms are falling victim to data breaches at an alarming rate, exposing sensitive client and attorney information. These incidents—most unpublicized before now—may just be the tip of the iceberg.
October 15, 2019 at 01:10 PM
12 minute read
In February 2017, tax forms for hundreds of current and former Jenner & Block employees fell in the wrong hands, potentially exposing their private addresses, Social Security numbers and salary information.
The law firm described the breach as a phishing incident, telling New York officials that files containing employees' W-2 forms were "mistakenly transmitted to an unauthorized recipient in response to what was believed to be a legitimate request from management."
In all, the breach may have exposed the personal information of 859 people, according to Jenner's report to state authorities.
That breach, previously unreported in the news media, was just one of dozens of cybersecurity incidents that law firms—from Big Law firms to solo offices—have reported to state authorities in the last five years, according to public records, interviews with affected firms, and cybersecurity experts.
Also in This Series: How Vendor Data Breaches Are Putting Law Firms at Risk
While Jenner's breach ostensibly only affected its own attorneys and employees, many other law firm breaches may have leaked confidential client information, reports to state officials show. Based on extensive public record requests, Law.com identified more than 100 law firms that have reported data breaches to authorities across 14 states since 2014, notifying authorities that a data breach affecting the firm could have exposed individuals' personal information.
Besides Jenner, Am Law 100 firm Proskauer Rose was also affected. Also falling victim to reported data breaches were Harris Beach, McGlinchey Stafford and other midsize firms; prominent boutiques such as Sanford Heisler Sharp; as well as solo practitioners, nonprofits and government law offices. Several law schools also reported breaches (as did ALM, Law.com's parent company).
Differences in reporting requirements across states make it difficult to discern definitive trends, but phishing attacks and other external breaches, such as hacking and vendor leaks, represented the largest share of the data breaches identified in Law.com's investigation.
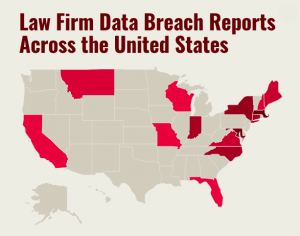 Click the image to see which law firms reported breaches.
Click the image to see which law firms reported breaches.Despite a number of high-profile breaches putting firms on notice of cyber risks in recent years, there are indications that law firm breaches are occurring more frequently, not less.
For instance, in New York state, the number of unique law firm data breaches doubled to eight in 2018 from four the previous year, affecting nearly 1,500 individuals, according to reports submitted by the firms.
Some cybersecurity lawyers and consultants said the reports likely represent a tiny fraction of the breaches affecting the legal industry. Law firms, like other privately held businesses, don't often publicize when their data is breached, and many may not report it to state officials, depending on the law.
Austin Berglas, former head of the FBI's cyber branch in New York and now global head of professional services at cybersecurity company BlueVoyant, said law firms are a top target among hackers because of the client information they possess.
"They are a one-stop shop," Berglas said. And because law firm success is often tied to their reputation for preserving attorney-client privilege, they may be more willing to pay hackers off if they fall victim to ransomware, he added.
"Law firms are only going to make those [data breach] reports when they've confirmed through a forensic investigation that reportable information has been touched. They're not going to report every event, every spearfishing campaign—they see it every day," Berglas said.
Breaching the Experts
Overall, disclosures by law firms and lawyers accounted for only a small fraction of the hundreds of data breach notifications that Law.com reviewed. Businesses ranging from accountants and restaurants to financial services firms to Trump hotels have notified state regulators that they may have been victims.
But the evidence of widespread legal industry breaches is striking because lawyers have a duty to protect privileged client information. And many law firms, particularly Am Law 200 firms, advertise themselves as experts in cybersecurity that advise clients on how to prevent and limit data breaches.
Some firms that market themselves as savvy in cybersecurity have been victims themselves. Jenner, for example, maintains a data privacy and cybersecurity practice for "counseling and litigation services to ensure the privacy and integrity of their sensitive information." In 2017, the same year Jenner reported its own phishing incident, the law firm informed state authorities of several data breaches on behalf of corporations such as Revlon Consumer Products, McKinsey & Co. and Scientific Games Corp.
In a statement to Law.com about its data breach, Jenner said the firm "complied with all legal and reporting requirements, and provided assistance to any affected personnel." The firm added that it "takes data security very seriously and maintains a rigorous and systematic approach to information security which includes technical, administrative and physical safeguards designed to protect client and other information." The firm added that it operates a "formal, documented, externally audited information security management system designed to protect firm and client data."
 Austin Berglas, former head of the FBI's cyber branch in New York, called law firms "a one-stop shop" for hackers. (Courtesy photo)
Austin Berglas, former head of the FBI's cyber branch in New York, called law firms "a one-stop shop" for hackers. (Courtesy photo)Proskauer Rose has also been both a counselor and a victim. The New York firm, which bills itself as a "recognized leader in privacy and cybersecurity law," has submitted data breach reports on behalf of Bed Bath & Beyond; Clinton Health Access Initiative; International Quality & Productivity Center; GAM Fund Management Limited; and Harry Winston, according to documents obtained by Law.com.
In 2016, Proskauer disclosed its own data breach to state authorities, after it "received several reports from firm employees that tax returns were filed in their names by unauthorized individuals in acts of identity theft."
The law firm reported to authorities and affected employees that an employee in its payroll department received a fraudulent email, appearing to be from one of the firm's senior executives, requesting copies of W-2s of firm personnel.
"Believing that the email request was legitimate," the firm told state officials, "the payroll employee emailed the requested information. The reply-to email address was fraudulent and the information was transmitted to an unauthorized third party."
In all, more than 1,500 people were affected, Proskauer said in its New York disclosure, including 700 state residents. Besides assisting its affected staff members, Proskauer reported that it was taking steps to "prevent something like this from happening again," including improving staff training and management controls and placing restrictions on the type of data that is electronically transmitted.
A Proskauer representative declined to comment to Law.com.
Discreet Reporting
All states require businesses to report cybersecurity incidents to individuals affected by the breach, but some states have minimal or no requirements for reporting to state officials. In the more regulated states, law firms, like other businesses, must be counted on to self-report.
"Law firms are pretty discreet on how they report" data breaches, said Claudia Rast, Butzel Long's cybersecurity group leader and a member of the American Bar Association's cybersecurity legal task force. "Unfortunately, many law firms don't report it. They don't want their clients to know about it."
Complicating matters, some of the most sensitive client data that law firms possess can be related to mergers and other transactions. But a breach involving details of an M&A deal, if it included corporate data but did not expose an individual's personal information, does not necessarily need to be reported to state authorities, according to Rast and others.
 Claudia Rast, who leads the cybersecurity group at Butzel Long, said many law firms don't report breaches to officials for fear of alarming clients. (Courtesy photo)
Claudia Rast, who leads the cybersecurity group at Butzel Long, said many law firms don't report breaches to officials for fear of alarming clients. (Courtesy photo)Such sensitive deal information was at the heart of the Manhattan U.S. attorney's indictment in 2016 of three Chinese nationals charged with hacking into two major U.S. law firms in a scheme to trade on information about imminent mergers and acquisitions. Based on details in the indictment, the two firms appeared to be Weil, Gotshal & Manges and Cravath, Swaine & Moore, firms with cyber breaches that were previously reported in the press. (Two defendants were never arrested and remain at large, while foreign officials denied the extradition of the third, said a spokeswoman for the U.S. Attorney's Office.)
In another high-profile incident, DLA Piper was hit by a major cyberattack in summer 2017, knocking out phones and computers across the firm, apparently triggered by a ransomware attack. A firm spokesman said "no client data was taken."
Still, an increasing number of breach reports filed by law firms in the last five years may show both the rising frequency of legal industry data breaches as well as an increasing awareness and compliance on the part of law firms, said lawyers in data privacy practices.
"There's more data breaches [in all industries], but more importantly people are becoming more sophisticated in monitoring" for them, said Avi Gesser, a partner at Davis Polk & Wardwell in its cybersecurity practice. "They're detecting them more, and they're more aware of their notification obligations as the market becomes more forgiving. People get more comfortable reporting. They feel like they are being good corporate citizens."
"If you don't call anybody or tell anybody," he said, "it's hard to play the victim role."
Phishing Breaches
Jenner and Proskauer were far from the only firms to report phishing attacks in the state records reviewed by Law.com. Indeed, data security experts said phishing schemes are the most common threat to law firms right now.
In what it described as a "crime against our firm," 217-attorney Harris Beach, based in Rochester, New York, reported that an "unauthorized individual" accessed a firm attorney's email last year, leading the firm to hire a computer forensic expert.
"The expert advises that the method used to access the email account automatically downloads the entire contents of the mail box to the hacker's personal computer, which makes it possible that the hacker still possesses the contents of this mail box and could make use of it in the future," the law firm wrote to state authorities.
The information of as many as 74 people, including name and Social Security number, could have been affected, according to the firm's letter.
Harris Beach spokesman Ben Rand acknowledged the phishing attack in a statement. "Our compliance, risk management and IT teams activated our response plan and took steps to contain, mitigate and resolve the incident," said Rand, adding that the firm informed law enforcement authorities. "Harris Beach is committed to safeguarding the confidentiality, integrity, and availability of client information," he said, and has adopted a "robust" cybersecurity program.
Prominent employment boutique Sanford Heisler Sharp reported to several states that an "unauthorized party obtained access to an email account" belonging to a firm partner, leading a "forensic investigation into a phishing incident." The data breach affected as many as 413 people, the firm told North Carolina authorities. A Sanford Heisler spokeswoman declined to comment.
In the case of McGlinchey Stafford, a 170-attorney New Orleans-based firm, the firm reported to New York state authorities about a year ago that information in an employee's email account may have been accessed by "an unauthorized third party as the result of a phishing attack," possibly affecting 468 people.
In a statement to Law.com, McGlinchey said it discovered the breach after learning that firm employees had received "spam emails." The firm said it "called on the expertise of outside consultants whose work was critical in minimizing the impact of the incident" and said there was no indication that the information was accessed or used by the unauthorized party.
"The firm has always upheld the highest standards in digital security, in part, because it's required by the financial services industry that we serve," McGlinchey said. "The systems we have in place greatly minimized this incident's potential impact."
In response to the incident, the firm said it reviewed and revised its policies, reset employees' access credentials, deployed a "more aggressive spam filter to all employee emails, and further implemented the use of advanced security protocols, including widespread use of multi-factor authentication."
"This incident confirmed for us that every ounce of resource we dedicate to shoring up our defenses and training our professional staff and attorneys is well spent," the firm added.
While the phishing incidents demonstrate that law firms can prepare and train lawyers to prevent some data leaks, other law firms' disclosures obtained by Law.com show that some security incidents may be totally out of their control.
Some law firms reported data breaches through a vendor's security lapse, while others reported stolen hard drives and laptops, raising the question of whether data breaches are a cost of doing business, even in an industry that so closely guards its information.
"More than half of businesses experience data security incidents," said Rast, the cybersecurity lawyer at Butzel Long. "Law firms are no different than most businesses out there."
This article is the first in a Law.com series focused on law firm data breaches. Next up: How firms' vendor relationships can create vulnerabilities.
Samantha Stokes contributed to this report.
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All
12-Partner Team 'Surprises' Atlanta Firm’s Leaders With Exit to Launch New Reed Smith Office
4 minute read
After Breakaway From FisherBroyles, Pierson Ferdinand Bills $75M in First Year
5 minute read
Wells Fargo and Bank of America Agree to Pay Combined $60 Million to Settle SEC Probe
Trending Stories
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250










