Ransomware Attacks in the Legal Profession
Here are the most essential actions to take to protect your organization from the effects of a ransomware attack.
May 26, 2020 at 01:39 PM
6 minute read

The legal profession has not escaped the insidious onslaught of ransomware attacks that propagate as if a digital pandemic. I have researched nearly 1,200 ransomware attacks, of which over 40 occurred within the legal profession. I say directly, as many hundreds of other law firms and court systems were indirectly affected when their managed service providers (MSP) such as TrialWorks (October 2019) and Epiq Global (March 2020) were attacked. The aftermath of these attacks ranged from lost access to critical trial data, trial postponements, and requests for delays in various court proceedings. Suddenly losing access to case management and e-Discovery systems can be catastrophic.
Everyone Is Fair Game
Ransomware victims include law firms, courts, and legal service providers. Of the 42 legal profession organizations affected by ransomware, law firms are at the top of the list.
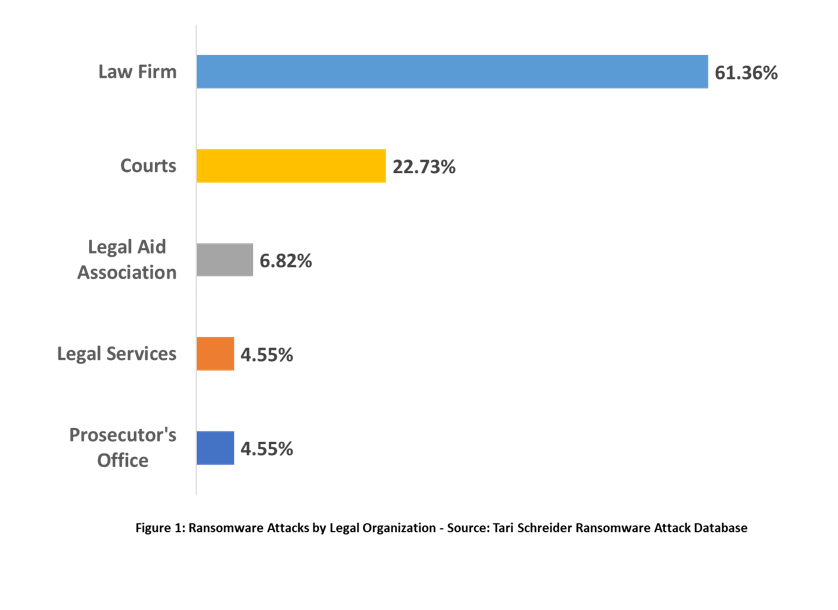
Size does not insulate an organization from the havoc a ransomware attack can inflict. Firms as large as $2.5 billion DLA Piper or a single attorney practice have experienced the effects of a ransomware attack. My research shows the average number of lawyers employed by law firms affected by ransomware is 180. The figure below shows how I classified the size of a law firms attacked by ransomware.
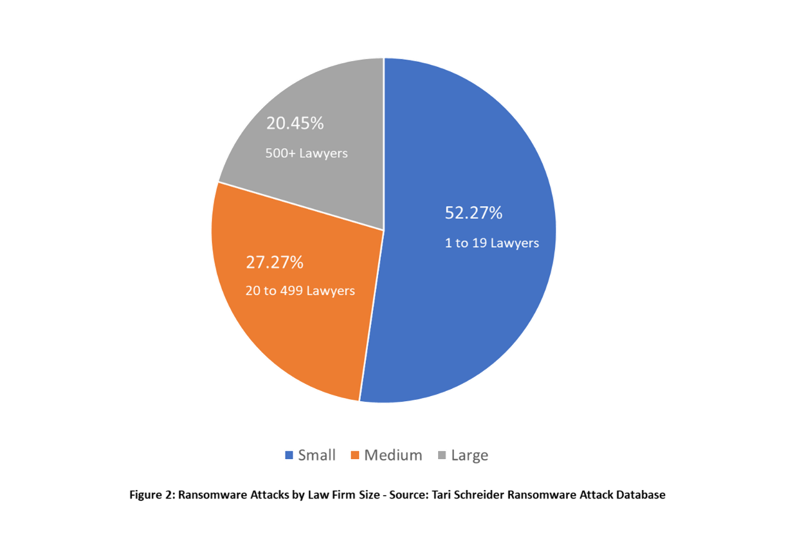
Ransomware operators view small law firms as having little to no security and in my experience, they would be correct.
To Pay or Not To Pay, That Is the Question
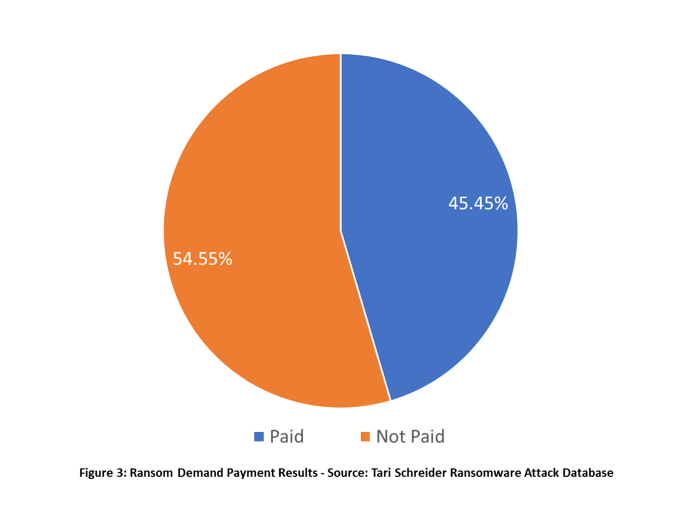
Ransomware is big business, with $45,337,368 in ransomware demands made of legal firms. This total number is skewed considering the recent ransom demand of $42 million made of the law firm to the stars, Grubman Shire Meiselas & Sacks. I fear the size of this one ransom demand will set the market for future demands and increase the number of attacks against law firms as ransomware operators seek large payouts. The average ransomware demand is currently standing at $1,054.368.
The legal profession is tight-lipped about ransom payouts. However, I learned 45% of organizations paid the ransom. This compares to approximately 12% of organizations who pay in other industries. I believe the higher rate of ransom payments in the legal profession is likely due to the lack of preparedness of legal organizations to defend against an attack.
Insurance as a Strategy?
Law firms that carry cyber insurance may not always be able to count on their policy to bail them out as one Rhode Island law firm found out in 2017. Moses Afonso Ryan, a Rhode Island litigation firm, made a claim to recover $700,000 in lost billable hours when ransomware locked their computer systems. The insurer denied the full claim stating only $20,000 was recoverable under the terms of the policy. The ultimate ruling the U.S. District Court for the District of Rhode Island would make in Moses Afonso Ryan LTD v. Sentinel Insurance Company could have a wide-reaching impact on the cyber insurance industry.
Terrible Tuesdays
Nearly 21% of legal industry ransomware attacks occur on Tuesday's whereas the most active day for ransomware attacks for all other industries is Friday at 22%.
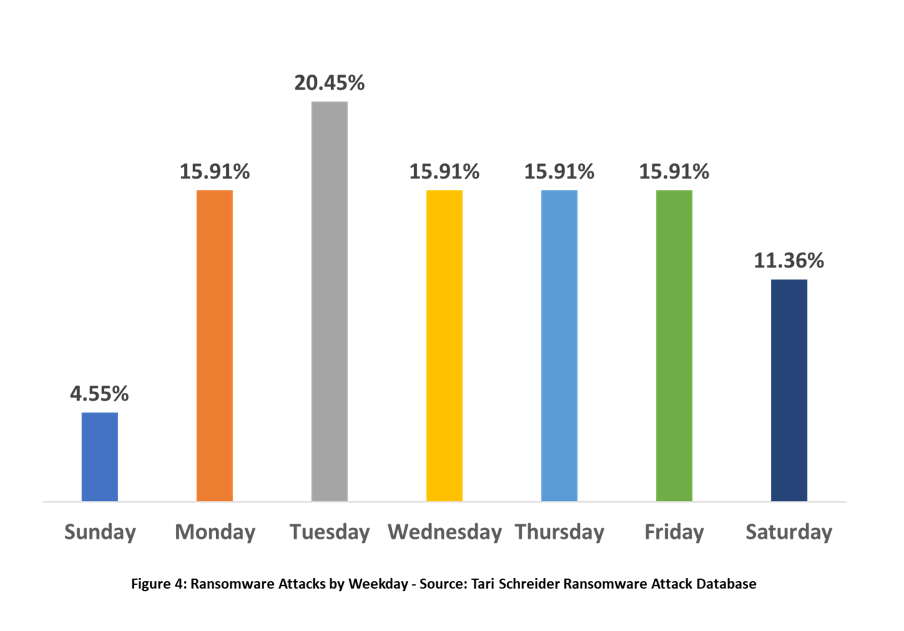
I cannot really account for this difference except to say that it is likely a statistical anomaly based on the dataset size.
Digital Quakes
Just as a single ransomware attack on an MSP can have a crippling ripple effect on multiple organizations so can an attack on an Office of the Courts. Take for instance the 2019 case when over 50 municipal courts dependent on the Georgia Administrative Office of the Courts (AOC) computer systems for case management were forced to resort to paper records causing cases to be postponed and some to even be dismissed. You need to ask yourself how depended you are on someone else's computer systems?
Abandon All Hope?
Never give up hope, as there is much that you can do. Here are the most essential actions to take to protect your organization from the effects of a ransomware attack:
- Create a Contingency Plan—Assume your cloud case management or e-discovery service provider or software is unavailable, plan to operate with paper documents and manual processes to handle time sensitive cases.
- Train Users to Avoid Becoming a Victim of a Phishing Attack—Train staff how to avoid falling for a targeted phishing attack through the use of phishing simulation software such as those offered by KnowBe4 and EC-Council. Email is the top threat vector for ransomware attacks.
- Backup Critical Data—Ensure all essential data is backed up with a strategy where the ransomware cannot also encrypt backup data. Follow the rule of 3-2-1 where three copies of your data are kept, data is stored on two separate storage devices and at least one copy of your data is stored off-site.
- Deploy Anti-Malware/Ransomware Software—A comprehensive endpoint protection solution that incorporates malware detection is essential to defending against ransomware attacks.
- Restrict User Privilege—Restrict privilege access to only employees who absolutely require system access. Ransomware attacks begin days before the actual attack, they linger in a system looking for privileged access to exploit their payload.
- Maintain Computer Hygiene—Many ransomware attacks exploit known vulnerabilities that can generally be patched to repel an attack. Disable all unnecessary ports and services as well as keep current with patching.
- Document Ransomware Response Plan—What you do in the minutes following an attack can be the difference in surviving or succumbing to an attack. You will need a step-by-step ransomware response plan.
Tari Schreider is the Author of Cybersecurity Law, Standards and Regulations—2nd edition, a master instructor of CISO certification courses for EC-Council, a Distinguished Technologist and former Chief Security Architect for Hewlett-Packard Enterprises. Mr. Schreider is board certified in cybersecurity, risk management and business continuity.
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All
AI Disclosures Under the Spotlight: SEC Expectations for Year-End Filings
5 minute read
A Blueprint for Targeted Enhancements to Corporate Compliance Programs
7 minute read

Three Legal Technology Trends That Can Maximize Legal Team Efficiency and Productivity
Law Firms Mentioned
Trending Stories
- 1Reviewing Judge Merchan's Unconditional Discharge
- 2With New Civil Jury Selection Rule, Litigants Should Carefully Weigh Waiver Risks
- 3Young Lawyers Become Old(er) Lawyers
- 4Caught In the In Between: A Legal Roadmap for the Sandwich Generation
- 5Top 10 Developments, Lessons, and Reminders of 2024
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250






