
Credit: Shutterstock.comBreaches of law firm data are not necessarily a flaw in their security.
Both Akerman and McDermott Will & Emery reported participants in their group health plans could have been affected by a widely reported Anthem cyber hacking in 2015. Akerman representatives did not respond to requests for comment. A McDermott representative declined to comment.
Jon Washburn, the chief information security officer at Stoel Rives, said the legal community has become more attuned to the risk of vendor threats, and many firms ramped up their efforts to address third-party risk.
Some law firms now require vendors that access, store, process or transmit confidential information be able to demonstrate through certifications or reports that the vendor has strong controls in place to reduce the risk of a data breach, he said.
In addition, some law firm clients are now including third- and even fourth-party risk management requirements in their outside counsel guidelines and representation agreements, Washburn said.
While law firms are often considered a weak point in the security of corporations' sensitive information, firms and their employees have frequently suffered potential leaks through their vendors, according to a Law.com investigation of law firm data breaches across the country. The breaches that law firms reported to state authorities varied in severity, and some incidents were unrelated to the strength of the law firm's cyber defenses and didn't risk or relate to client data.
External breaches, including phishing and hacking as well as vendor incidents, were the most commonly identified source of data exposure events reported by law firms. A review of data breach notifications from more than a dozen states found stolen or lost devices were the second most common type of security incidents reported by law firms.
[falcon-embed src="embed_1"]
In 2016, Philadelphia litigation boutique Goldberg, Miller & Rubin reported it learned a security researcher was able to access electronic files on some of its cases. It appeared a "service provider made an error in configuring the backup device," the firm told state authorities. A partner at Goldberg Miller declined to comment.
"We have the data because we represented you or another party in a claim or lawsuit," the firm said in a notification letter to those affected.
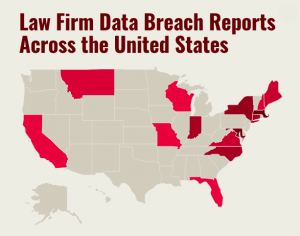 Click the image to see which law firms reported breaches.
Click the image to see which law firms reported breaches.According to Law.com's analysis, several large firms reported their employees were potentially affected through corporate breaches that made national news. For instance, Jones Day reported an unauthorized individual gained access to the reservation system of Sabre Hospitality Solutions, a third-party vendor for the firm's travel services provider, between August 2016 and March 2017.
"This was not an incident that was suffered by the firm or by our travel agency, it was by a vendor of the travel agency," Jones Day partner Mauricio Paez said in an interview, adding his firm submitted a security report to comply with state law.
The firm continues to "vet any third-party provider for their own security controls and information security program," Paez said.
Complex and Routine
Besides external breaches, law firm data security incidents ran the gamut from ransomware attacks to stolen hard drives to mail mixups, according to the data breach reports obtained by Law.com.
Some data breaches were surprisingly sophisticated in capturing client data.
Texas boutique Schachter Harris reported in 2017 that it was subject to an attack by "unknown criminals" that could have affected people who filed or were involved in lawsuits alleging asbestos-related injuries.
"The attackers used encryption ransomware to make some information on our computers inaccessible to us," the firm told authorities. "When we did not pay the ransom, the criminals claimed to possess the data from our computers. Based on our investigation, we believe that the attackers were able to acquire some files stored by our firm, relating to at least one of our clients."
Partner Ray Harris said "this was a serious crime" and "the criminals to our knowledge have not been caught." The firm declined to comment further.
Some law firm thefts were also reported to have exposed client data. One of the largest law firm breaches Law.com found based on the number of people affected was at a Los Angeles criminal defense firm, Imhoff & Associates, which notified authorities in at least six states that a hard drive containing backup files was stolen from an employee's locked car trunk.
In its notification letter, Imhoff, which worked with Santa Monica police and forensic experts, said, "The hard drive may have contained files with differing amounts of employee and client information," such as Social Security numbers, driver's license numbers and contact information. The firm told New York officials that personal information from 13,026 people could have been exposed.
In an interview, managing director Vincent Imhoff said he didn't "think any information was actually breached" and acknowledged he was the theft victim. Imhoff said his firm has changed the way it stores information, declining to discuss details. He said his firm has been working with a third party to ensure cybersecurity since 2016.
As the Imhoff event demonstrated, some of the most troubling security incidents occurred when law firms never learned what happened to missing devices.
Not all data breaches were malicious or deliberate widespread attacks. Several law firms reported paperwork errors by firm employees and attorneys, such as sending the wrong document to a client or inadvertently including personal information in a court document.
Squire Patton Boggs informed state authorities last year that, when mailing out tax forms, it "mistakenly" mixed up documents in an envelope, possibly affecting 256 people.
Ultimately, whether the breach flows from a cunning hack or a misplaced laptop, law firms often responded the same way: hiring forensic experts to track and assess the exposure, training staff on prevention and implementing new cybersecurity guidelines since criminals and hackers are becoming more sophisticated.
"They're moving at an equal pace," said Claudia Rast, Butzel Long's cybersecurity group leader and a member of the American Bar Association's cybersecurity legal task force. "The bad guys are moving as quickly as we are."
Samantha Stokes contributed to this report.
Read More:
More Than 100 Law Firms Have Reported Data Breaches. And the Problem Is Getting Worse
Law Firm Cybersecurity: See Which Firms Reported a Data Breach
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All
SEC Whistleblower Program: What to Expect Under the Trump Administration
6 minute read
Turning the Shock of a January Marital Split Into Effective Strategies for Your Well-Being
5 minute read
Latest Boutique Combination in Florida Continues Am Law 200 Merger Activity
3 minute read
South Florida Real Estate Lawyers See More Deals Flow, But Concerns Linger
6 minute readTrending Stories
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250






