Benchmarking Cybersecurity: CISO Perspectives on Managing Evolving Global Risks
By emphasizing training, communicating effectively, and acknowledging the increased influence of the cloud, companies of all sizes in most industries are succeeding in greater numbers.
March 12, 2018 at 08:00 AM
11 minute read

This article appeared in Cybersecurity Law & Strategy, an ALM publication for privacy and security professionals, Chief Information Security Officers, Chief Information Officers, Chief Technology Officers, Corporate Counsel, Internet and Tech Practitioners, In-House Counsel. Visit the website to learn more.
In a hyperactive security landscape, new threats often emerge faster than organizations can mount defenses. While they routinely create solutions to rapidly combat information uncertainty, security leaders are battling a relentless foe on multiple fronts. By combining tools, teams and tenacity in the face of a shifting regulatory environment and a complex business climate, they are beginning to acclimate to the perpetual uncertainty that now characterizes the modern economy.
To help them benchmark information management protocols, insider threat practices, security investments, and an array of issues that impact an organization's data protection techniques, Ankura Consulting commissioned Ari Kaplan Advisors to engage 30 security leaders, 70% of whom were their company's chief information security officer (CISO), in a collective conversation about the cross-functional solutions they are applying to today's most complex challenges and the creative ways they are adapting to a perilous threat landscape.
Ari Kaplan Advisors conducted the interviews by telephone, under condition of anonymity, in August of 2017. While most participants were based in the United States, the report includes perspectives from Europe and Australia. Given that 67% of the respondents were from the highly-regulated financial services and life sciences industries, the responses skew toward strong levels of awareness about cybersecurity and data governance, though a review of the remaining third from non-regulated industries reflects a more measured viewpoint.
Seventy percent of the participants were from organizations with over $1 billion in annual revenue, and 50% were from companies with revenues of more than $5 billion. Eighty percent were from companies with over 5,000 employees. They hailed from a diverse group of industries, including: financial services (30%); health care (16.7%); technology (16.7%); banking (10%); insurance (10%); consulting (3.3%); manufacturing (3.3%); media (3.3%); telecommunications (3.3%); and retail (3.3%).
The excerpts below from the findings reflect that security leaders are ultimately working toward building and sustaining cross-functional programs by improving both processes and technologies.
The Results
The Evolving Role of the CISO
Eighty percent of respondents work in organizations that employ a CISO, and 23% have a CSO as well. Fifty-three percent of CISOs report to the chief information officer, 7% report directly to the chief executive officer, and the remaining participants report to their chief operating officer, chief risk officer, or another senior-level individual at the company. Fifty-seven percent report to senior management at least monthly, while 37% do so quarterly. Forty-three percent of participating CISOs report to their board of directors on a quarterly basis, while 20% do so monthly, 13% semi-annually, and 10% annually.
CISOs Are Cautiously Adapting to the Cloud
Eighty-seven percent of the respondents reported that they rely on vendors or cloud hosting providers to generally host non-critical information to save money and streamline their operations. Some are also trying to upgrade their infrastructure and respond to an enterprise-wide initiative to innovate. Seventeen percent of the respondents noted that Office 365 is a common impetus for moving to the cloud.
Outside Support Is Essential
One-hundred percent of respondents work with third parties to support their security initiatives and 87% use third parties for ongoing project or program support. While 97% formally evaluate the security practices of their vendors, partners, law firms and third parties that interact with their data, 60% of respondents do not extend this level of inquiry to the partners of their third parties.
Managed Services Providers Typically Support Cybersecurity
Seventy-seven percent of respondents advised that the scope of their managed security services includes incident response. And, for 63%, that support included onsite response. Thirty-seven percent were confident that their managed services provider would provide a legally defensible investigation if they were the victim of a breach or other cyber incident. Thirty percent claimed to be very confident.
Security and BYOD Policies Abound
One-hundred percent of the respondents reported having data security and incident response plans. All of the respondents noted that they have a privacy policy or program, but 13% described it as “insufficient or incomplete.” Eighty-seven percent reported that their organizations have both a disaster recovery plan and a data governance framework or committee in place. Eighty percent reported having a Bring Your Own Device (BYOD) plan, though some noted that their plan is to prohibit personal devices; 63% believe that those gadgets contain company sensitive information.
Security Messaging Is Evolving with Training and Communication Trends
While 93% reported focusing their messaging on being part of the solution, 20% still claimed to leverage fear to grab the attention of their employees. Despite the 20% who choose fear, a number of security leaders provided reasons for avoiding it, 20% also noted offering best practices to avoid risk.
Success of Security Investments Is Measured by Risk Reduction
Ninety-three percent of respondents focus on risk reduction as a measure of the return on their IT security investments, followed by 70% interested in improved detection capabilities. While 57% characterized the amount they had spent on IT security in the past two years as sufficient, 20% advised that it has been insufficient.
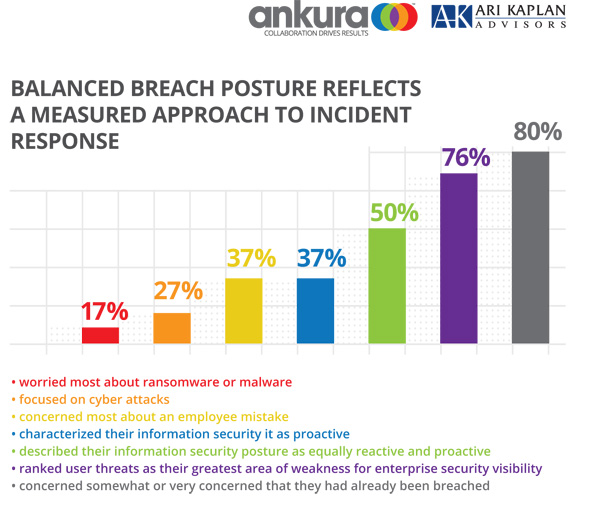
Balanced Breach Posture Reflects a Measured Approach to Incident Response
Fifty percent of the respondents described their information security posture as equally reactive and proactive, with an additional 37% characterizing it as proactive. Eighty percent of the respondents were somewhat concerned or very concerned that they had already been breached; 37% were most concerned about an employee mistake, followed by 27% focused on cyber attacks, and 17% most worried about ransomware or malware. And, 76% ranked user threats as their greatest area of weakness for enterprise security visibility.
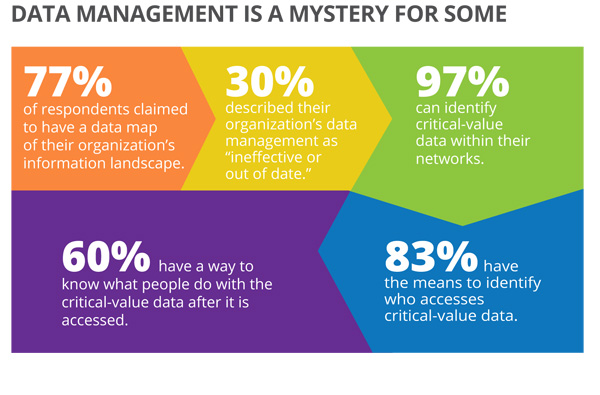
Data Management Is a Mystery for Some
Although 77% of respondents claimed to have a data map of their organization's information landscape, 30% described it as “ineffective or out of date.” Fifty-seven percent of the respondents advised that conducting a data identification study to map and evaluate their existing data stores in the next year would add the most value to the security road map of their respective organizations. And, while 97% can identify critical-value data within their networks and 83% have the means to identify whom within their organization accesses that critical value data, only 60% have a way to know what people do with the critical value data after they have accessed it.
Looking Forward
More Financial Services Companies Will Hire CISOs or Engage Virtual CISOs
The participants reported that the median number of external providers who support them was seven to 10. “We outsource most of the work that the internal technology team does not have time to do,” said the CISO for a smaller financial services institution. For the 20% of respondents who do not have a CISO, the CTO, COO, or deputy security official assumes that role. Forty percent of those companies have revenue under $1 billion.
Also, 40% of the respondents noted that they are subject to 23 NYCRR 500, the state of New York's new Cybersecurity Requirements for Financial Services Companies, which mandates that a company designate a CISO, either internally or from an external resource. It is likely that the role of the CISO will continue to become more prominent. This is particularly important for smaller companies without a CISO that now need to either hire one on a full-time basis or engage a third party to provide those services.
Data Mapping Is Likely to Expand
Although 77% of respondents work for organizations that maintain data maps, 30% of them described those documents as ineffective or out of date. As a result, it is likely that they will update existing records and more companies will develop them, given the challenges associated with the data landscape. “We would desperately love to do that and are making baby steps,” reported a bank CISO. “It is the ultimate blind man feeling an elephant, as it describes a situation that is so big, but you have no idea how to get started,” the individual added. A CISO with an insurance company highlighted that the regulatory environment is also driving the importance of this effort. “Encryption at rest is required by the New York regulations, and in order to do that, you need a data map.”
Clarity May Characterize Cyber Liability Insurance
While 83% of the participating CISOs advised their companies on the purchase of cyber liability insurance and 67% maintain such policies, there is a consistent call for clarity in these agreements. As the size, scope, and frequency of these claims rise, the documents may provide a more thorough outline of the coverage limitations going forward. “The cyber policies we've reviewed have so many waivers and limitations within them that if we had a breach, they would not cover us,” said a healthcare CISO. “We have looked at them and have gone through the exercise of evaluating peers because when you assess the items that they exempt, we did not feel like we were getting our money's worth; we would rather be self-insured,” added another in the insurance industry.
Focus on New Regulations, Including GDPR, Should Rise
Since 73% of respondents noted that regulators are driving their IT security budgeting decisions (and that was 20% more than the next most significant factor, i.e., the value of their data), and that 100% of the participants advised that there is at least one regulatory framework that applies to their business, the focus on an increasingly dynamic regulatory environment is likely to rise. Most important, since 60% of those surveyed noted that GDPR is important to their organizations and 87% have a privacy policy or program, given the global interest in the new framework and its impending May 2018 enforcement date for non-compliance violations, organizations are likely to concentrate on its influence more closely in the coming months.
Insider Threat Programs and Policies May Increase
While 63% of the respondents have an insider threat program or policy, this number is likely to increase, especially since an employee mistake was the security incident about which the largest number of respondents (37%) were concerned. One financial services CISO noted: “An insider threat could encompass an employee mistake, a cyber attack, or a malware attack.” In addition to the uncertainty associated with employee behavior, many organizations have weak data policies in general. “The data stuff is usually completely out of the control of the security team; most of the time, nobody has control of it, which is part of the problem,” said a CISO in financial services. The combination of fragile information governance coupled with the prominence of insider threats increases the likelihood that more organizations will develop strategies to combat this potent combination.
Uncertainty in today's cybersecurity landscape is not slowing positive change in information management, emerging threat response, and global data protection efforts. Most organizations recognize the need for security influence in the C-suite, all have incident response plans, and almost everyone in this area recognizes the value of investing in infrastructure to promote risk reduction. By emphasizing training, communicating effectively, and acknowledging the increased influence of the cloud, companies of all sizes in most industries are succeeding in greater numbers. This trend will continue if organizations prioritize informing leadership, applying a successful risk management strategy, and collaborating with strong cybersecurity partners.
Jessica Block is a senior managing director at Ankura Consulting based in Washington, DC, and leads the firm's data governance practice. She has more than 15 years of experience working with companies and counsel facing complex information management challenges. Ari Kaplan is a legal industry analyst and the principal of Ari Kaplan Advisors. He is a member of this newsletter's editorial advisory board.
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View AllTrending Stories
- 1Gunderson Dettmer Opens Atlanta Office With 3 Partners From Morris Manning
- 2Decision of the Day: Court Holds Accident with Post Driver Was 'Bizarre Occurrence,' Dismisses Action Brought Under Labor Law §240
- 3Judge Recommends Disbarment for Attorney Who Plotted to Hack Judge's Email, Phone
- 4Two Wilkinson Stekloff Associates Among Victims of DC Plane Crash
- 5Two More Victims Alleged in New Sean Combs Sex Trafficking Indictment
Who Got The Work
J. Brugh Lower of Gibbons has entered an appearance for industrial equipment supplier Devco Corporation in a pending trademark infringement lawsuit. The suit, accusing the defendant of selling knock-off Graco products, was filed Dec. 18 in New Jersey District Court by Rivkin Radler on behalf of Graco Inc. and Graco Minnesota. The case, assigned to U.S. District Judge Zahid N. Quraishi, is 3:24-cv-11294, Graco Inc. et al v. Devco Corporation.
Who Got The Work
Rebecca Maller-Stein and Kent A. Yalowitz of Arnold & Porter Kaye Scholer have entered their appearances for Hanaco Venture Capital and its executives, Lior Prosor and David Frankel, in a pending securities lawsuit. The action, filed on Dec. 24 in New York Southern District Court by Zell, Aron & Co. on behalf of Goldeneye Advisors, accuses the defendants of negligently and fraudulently managing the plaintiff's $1 million investment. The case, assigned to U.S. District Judge Vernon S. Broderick, is 1:24-cv-09918, Goldeneye Advisors, LLC v. Hanaco Venture Capital, Ltd. et al.
Who Got The Work
Attorneys from A&O Shearman has stepped in as defense counsel for Toronto-Dominion Bank and other defendants in a pending securities class action. The suit, filed Dec. 11 in New York Southern District Court by Bleichmar Fonti & Auld, accuses the defendants of concealing the bank's 'pervasive' deficiencies in regards to its compliance with the Bank Secrecy Act and the quality of its anti-money laundering controls. The case, assigned to U.S. District Judge Arun Subramanian, is 1:24-cv-09445, Gonzalez v. The Toronto-Dominion Bank et al.
Who Got The Work
Crown Castle International, a Pennsylvania company providing shared communications infrastructure, has turned to Luke D. Wolf of Gordon Rees Scully Mansukhani to fend off a pending breach-of-contract lawsuit. The court action, filed Nov. 25 in Michigan Eastern District Court by Hooper Hathaway PC on behalf of The Town Residences LLC, accuses Crown Castle of failing to transfer approximately $30,000 in utility payments from T-Mobile in breach of a roof-top lease and assignment agreement. The case, assigned to U.S. District Judge Susan K. Declercq, is 2:24-cv-13131, The Town Residences LLC v. T-Mobile US, Inc. et al.
Who Got The Work
Wilfred P. Coronato and Daniel M. Schwartz of McCarter & English have stepped in as defense counsel to Electrolux Home Products Inc. in a pending product liability lawsuit. The court action, filed Nov. 26 in New York Eastern District Court by Poulos Lopiccolo PC and Nagel Rice LLP on behalf of David Stern, alleges that the defendant's refrigerators’ drawers and shelving repeatedly break and fall apart within months after purchase. The case, assigned to U.S. District Judge Joan M. Azrack, is 2:24-cv-08204, Stern v. Electrolux Home Products, Inc.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250






