The 'Sippy Cup' Problem: Redefining Cybersecurity Awareness
The best employees cannot keep your organization safe if they do not know how. Taking stock of the human dimension, the reality is that your employees are not all as cyber-aware as you think.
May 28, 2020 at 10:30 AM
9 minute read
 SANS Institute
SANS Institute
One of the more immediate implications of the COVID-19 pandemic has been the almost forced adoption of tele-interactions and virtual processes. Jurisdictions are now holding court via virtual courtrooms. Considering this fact within the existing context of an evolving digital world, there is a spectrum of vulnerabilities that will warrant increasing attention.
Irrespective of the pervasiveness of malware attacks, network breaches, and ransomware activities that make headlines, the human element is a fundamental variable that is common to all cybersecurity events. As a root cause, federal and state governments have one critical issue in common—"cyber awareness" amongst their general workforces.
The requirement to remote work has effectively been instituted overnight and will continue to increase as an operational demand and expectation as social distancing measures continue. As such, when an organization makes a conscious, planned or forced choice to "go remote" they must account for cybersecurity. The concept of "cyber awareness" masquerades with a disarmingly cute and safe new face that actually functions to undermine its core significance to cybersecurity—a problem we are identifying as the "sippy cup." While seemingly protective, the sippy cup gives organizations the illusion of protection, however cyber criminals continue to exploit the lack of situational awareness.
What is the "Sippy Cup" Problem?
The home has become the new workplace, which has presented new and unexpected challenges to daily life. This new working environment, with its host of home distractions, operational workarounds, and process inefficiencies, has come to represent aggregate barriers and risks to cyber awareness and cybersecurity on the whole. Taking the business analogy of the sippy cup, i.e., where the sippy cup "protected" the immediate environment from a toddler spilling its contents, cyber awareness training and policies presumably "protected" organizations from cyber incidents imprudently triggered by unsuspecting employees. Necessarily, this simplistic view of a basic "people problem" needs to be redefined and updated using science.
Specifically, the reliance of organizational cybersecurity on employees' keen sense of cyber awareness can be defined by the three dimensions of cyber awareness where organizations provide actionable knowledge to their employees, affect their attitudes toward cybersecurity, and consequently effect a behavioral shift in their cyber interactions. These three dimensions constitute the knowledge (K), attitude (A), and behavior (B) or K-A-B cyber awareness model. The sippy cup represents the unknown and unexpected challenges we face now being acutely brought to the surface because of the "new normal" of global remote work but one that existed long before COVID-19. Cybersecurity includes a three-year-old with a sippy cup in our home—we just did not realize that three-year-old is us.
Nobel Laureate Richard Feynman once said that "the first principle is that you must not fool yourself—and you are the easiest person to fool."
The Human Factor
Poet Alexander Pope said, "[t]o err is human, to forgive divine. We all commit sins and make mistakes." Over 300 years later, that statement has never been more accurate. Humans are fallible. No matter the nature, scope, or extent of an organizational cybersecurity event, invariably at some point along the series of pre-episode events is an action, taken wittingly or unwittingly, by an individual inside the organization. Every aspect of securing, defending, and attacking has a human element, an element that profoundly affects all the other components and guarantees that there can be no silver bullet in cybersecurity, which is why there is no tech-only solution. We are only as strong as the weakest link, i.e., the end user.
The best employees cannot keep your organization safe if they do not know how. Taking stock of the human dimension, the reality is that your employees are not all as cyber-aware as you think. That is the role of risk management.
Risk Management
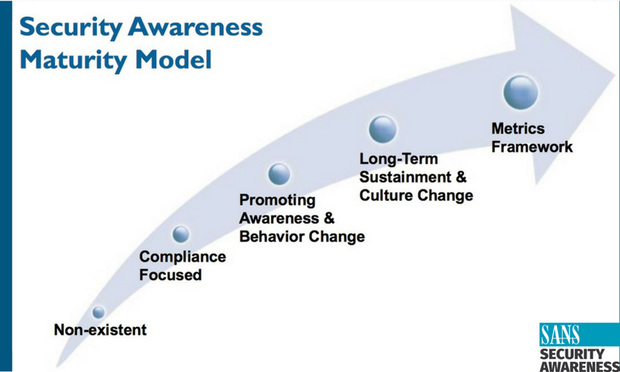
Cybersecurity awareness is an important and amplifying component of an organization's overall risk management. The SANS Institute's Security Awareness Maturity Model, a leading cybersecurity educational institution, illustrates the role of deliberate promotion of awareness and behavior change (image above).
Employees need to be able to recognize risks and respond appropriately. Employers need to teach them how by raising their situational awareness and keeping it high. All security awareness training attempts to do this, but training programs fail because they lose the human component to training. Organizations rely on video training where employees are not engaged in the training. Employees see this type of training as something they have to do; a box they have to check for their employer. Thus, it is common to find organizations that are hacked have "trained" their employees but have not created a strong cybersecurity and data privacy program. This is proof that such training programs lack the vital effectiveness necessary to protect an organization.
In some organizations, the challenge of identifying these rogue elements has resulted in attempts at "zero trust" environments. A "zero trust" environment is where the policies and technology around those policies is so restrictive that no one is "trusted." Restrictive security policies may seem to be a valid strategy, but users are often unaware of how those policies affect their job. End users are trained on general security, and not the restrictive policies themselves. If the end user is taught about cybersecurity but not on how it impacts their job, they are not functionally aware of how cybersecurity affects the way they work. In plain language, policies need to be tailored to departments, and end user job functions. This is the way to create an effective security and privacy program. Having rote policies accomplishes nothing besides hampering innovation and impeding productivity.
The lack of cybersecurity awareness had catastrophic effects in breaches like Equifax, Marriott/Starwood Hotels, police stations across the country, schools, and Barbara Corcoran, from Shark Tank, losing $400K. We have seen no matter how much organizations spend on cybersecurity "infrastructure," the human factor remains. Courts need to recognize the human variable, the "awareness factor" of court staff. Knowing there is a human variable and tracking that variable are two different matters; quantification is necessary.
The Need for Quantification
In light of the sippy cup problem, a new face for cybersecurity awareness needs to be measured, resolved, and/or mitigated in order to continue to provide justice, secure assets, minimize liabilities, and increase positive growth.
Your privacy and security program needs to incorporate security awareness. This ensures employees are informed and aware of security risks, thereby protecting themselves and an organization's assets. In order for a security awareness program to add value to an organization, it is necessary to have a set of methods to study and measure its effect.
Analytics and the rise of artificial intelligence make spotting potential insider threats easier and less intrusive. However, even with advances in technology, managers need to be aware of what to look for and how to focus their security efforts to get the greatest returns on protection:
- Understand your assets,
- Know your people,
- Apply analytics,
- Cover the basics, and
- Train.
The interplay among the K-A-B dimensions is commonly in effect during the course of employees' daily routines. There are quantitative and qualitative features of the K-A-B model that ultimately constitutes a person's cyber awareness. The knowledge component entails core requirements which a person either knows or does not know. In contrast, tailored behavioral analyses allow for the revelation of underlying attitudes and the situational actions that one takes in response to defined stimuli. This is where Implicit Association Testing (IAT) has proven to be a valuable tool to reveal hidden or subconscious biases in attitude. This combined with objective situational assessments that include a time component together provide a powerful insight into a person's response to various cyber threats. CISO's will find this information essential to develop custom training programs tailored according to employees' environment and job responsibilities.
Cyber criminals leverage sophisticated behavioral psychology principles to socially engineer cyber threats that are designed to exploit relative weaknesses in a person's cyber knowledge, attitude, and behavior during certain situations where their cyber awareness is functionally at its lowest. Traditional cybersecurity training programs characterized by videos and didactics do not improve a person's cyber awareness because they do not account for situational risk and behavioral psychology, which are part of the employee's work environment.
Cybersecurity awareness is critical to our courts. Courts have an obligation to ensure that staff know and understand the way cybersecurity and privacy impact their day-to-day operations. The first step is quantification.
Putting It together
Once the knowledge (K), attitude (A), and behavior (B) of your organization are measured, the next step is to have directed actions. This data will be utilized to provide a personalized cybersecurity awareness training program.
Personalized training combined with corporate policies and cybersecurity awareness is the starting point of measuring and changing your organization's K-A-B.
Cybersecurity awareness would be measured yearly, accounting for changes, as society, pandemic response, and the cybersecurity industry continue to evolve and respond to newer, more automated cyberattacks.
The sippy cup problem is the new face for cybersecurity awareness which includes measurement, mitigation, and resolution of gaps, specifically knowledge, attitude, and behavior. The sippy cup represents all of us, our cybersecurity "awareness," and our ability to provide justice in this modern and remote world.
Sajed ("Saj") Naseem is the Chief Information Security Officer (CISO) of New Jersey Courts. Rebecca L. Rakoski is the co-founder and managing partner at XPAN Law Group, a boutique law firm focusing on cybersecurity, data privacy, and electronic discovery.
This content has been archived. It is available through our partners, LexisNexis® and Bloomberg Law.
To view this content, please continue to their sites.
Not a Lexis Subscriber?
Subscribe Now
Not a Bloomberg Law Subscriber?
Subscribe Now
NOT FOR REPRINT
© 2025 ALM Global, LLC, All Rights Reserved. Request academic re-use from www.copyright.com. All other uses, submit a request to [email protected]. For more information visit Asset & Logo Licensing.
You Might Like
View All
Send Us Your New Partners for the NJ Law Journal's New Partners Yearbook
1 minute read
New Methods for Clients and Families to Have Their Estate and Legacy Planning Complete
5 minute read
Tensions Run High at Final Hearing Before Manhattan Congestion Pricing Takes Effect
4 minute readTrending Stories
Who Got The Work
Michael G. Bongiorno, Andrew Scott Dulberg and Elizabeth E. Driscoll from Wilmer Cutler Pickering Hale and Dorr have stepped in to represent Symbotic Inc., an A.I.-enabled technology platform that focuses on increasing supply chain efficiency, and other defendants in a pending shareholder derivative lawsuit. The case, filed Oct. 2 in Massachusetts District Court by the Brown Law Firm on behalf of Stephen Austen, accuses certain officers and directors of misleading investors in regard to Symbotic's potential for margin growth by failing to disclose that the company was not equipped to timely deploy its systems or manage expenses through project delays. The case, assigned to U.S. District Judge Nathaniel M. Gorton, is 1:24-cv-12522, Austen v. Cohen et al.
Who Got The Work
Edmund Polubinski and Marie Killmond of Davis Polk & Wardwell have entered appearances for data platform software development company MongoDB and other defendants in a pending shareholder derivative lawsuit. The action, filed Oct. 7 in New York Southern District Court by the Brown Law Firm, accuses the company's directors and/or officers of falsely expressing confidence in the company’s restructuring of its sales incentive plan and downplaying the severity of decreases in its upfront commitments. The case is 1:24-cv-07594, Roy v. Ittycheria et al.
Who Got The Work
Amy O. Bruchs and Kurt F. Ellison of Michael Best & Friedrich have entered appearances for Epic Systems Corp. in a pending employment discrimination lawsuit. The suit was filed Sept. 7 in Wisconsin Western District Court by Levine Eisberner LLC and Siri & Glimstad on behalf of a project manager who claims that he was wrongfully terminated after applying for a religious exemption to the defendant's COVID-19 vaccine mandate. The case, assigned to U.S. Magistrate Judge Anita Marie Boor, is 3:24-cv-00630, Secker, Nathan v. Epic Systems Corporation.
Who Got The Work
David X. Sullivan, Thomas J. Finn and Gregory A. Hall from McCarter & English have entered appearances for Sunrun Installation Services in a pending civil rights lawsuit. The complaint was filed Sept. 4 in Connecticut District Court by attorney Robert M. Berke on behalf of former employee George Edward Steins, who was arrested and charged with employing an unregistered home improvement salesperson. The complaint alleges that had Sunrun informed the Connecticut Department of Consumer Protection that the plaintiff's employment had ended in 2017 and that he no longer held Sunrun's home improvement contractor license, he would not have been hit with charges, which were dismissed in May 2024. The case, assigned to U.S. District Judge Jeffrey A. Meyer, is 3:24-cv-01423, Steins v. Sunrun, Inc. et al.
Who Got The Work
Greenberg Traurig shareholder Joshua L. Raskin has entered an appearance for boohoo.com UK Ltd. in a pending patent infringement lawsuit. The suit, filed Sept. 3 in Texas Eastern District Court by Rozier Hardt McDonough on behalf of Alto Dynamics, asserts five patents related to an online shopping platform. The case, assigned to U.S. District Judge Rodney Gilstrap, is 2:24-cv-00719, Alto Dynamics, LLC v. boohoo.com UK Limited.
Featured Firms
Law Offices of Gary Martin Hays & Associates, P.C.
(470) 294-1674
Law Offices of Mark E. Salomone
(857) 444-6468
Smith & Hassler
(713) 739-1250







